phishing
Overview
The word phishing refers to any attempt to obtain sensitive data – most commonly username/password combinations – by posing as a legitimate web site with whom the phishing victim has an account.
The most common scenario goes like this:
- User receives an email apparently from a legitimate business with whom s/he has an account
- The email informs the user that s/he needs to log onto her/his account for some reason
- The email gives a "convenient" log-on link for the user
- some early phishing attempts included a log-on form in the email itself, but now too many people have become aware that this is a warning flag
- The URL in the link usually includes some text which looks like the legitimate site's log-in URL, and may even be indistinguishable from a legitimate URL unless the user knows a little bit about how URLs work
- The user clicks on the link, and is shown a page which appears identical to the legitimate log-in page (although links on this page may or may not function), but which is actually hosted on a machine controlled by the phisher
- The user enters her/his log-in information, and presses the "log in" button
- The user's username and password are recorded by the phisher, who later uses them to break into the user's account
- The site may then allow the user to actually log in (by passing the username and password on to the real site), or may report some legitimate-seeming "temporary error" and advise the user to try again later.
Phishing sites are a form of malware.
Example
Woozle received the following email on 2007-05-26 (edited for proper display within this wiki page):
|
Dear Paypal member, Paypal was notified by Visa and Mastercard that some members card information This breach is not associated with Paypal computer systems. If your card number has been compromised you will be notified by phone and/or e-mail. Please note that failure to reply within 2 days will result in permanent cancelation of your account with Paypal Click on the following link to remove this temporary block placed on your account Sincerely, Copyright © 1999-2006 PayPal. All rights reserved. |
Notice the bad punctuation and formatting, highly atypical of official messages from a large company such as PayPal.
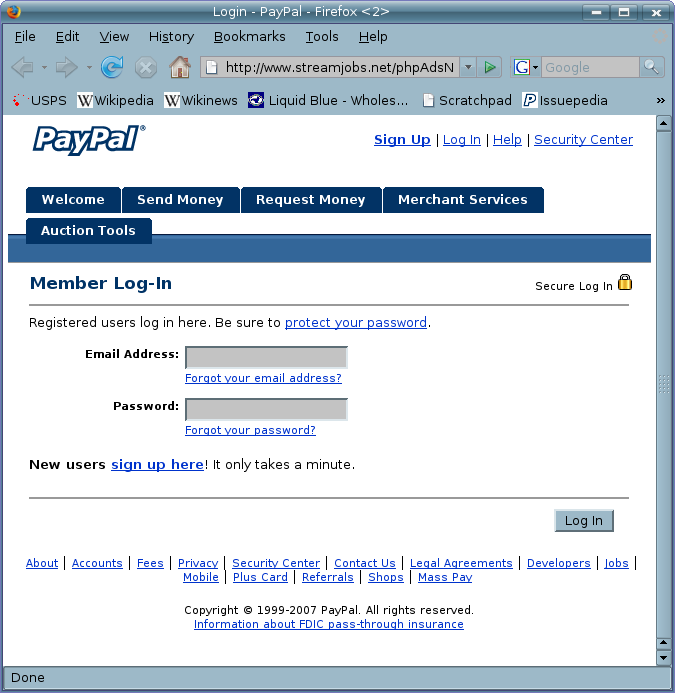
web site
As an imitation, this is somewhat outdated; the real PayPal site currently looks like this.
None of the links work; they all seem to link to "#", which just refers back to the same page. (There isn't any javascript.)
whois
A whois on streamjobs.net (where the phishing page is hosted) returns this:
Domain Name: STREAMJOBS.NET Registrar: MELBOURNE IT, LTD. D/B/A INTERNET NAMES WORLDWIDE Whois Server: whois.melbourneit.com Referral URL: http://www.melbourneit.com Name Server: NS1.GLOBALSERVERS.COM Name Server: NS2.GLOBALSERVERS.COM Status: ok Updated Date: 18-oct-2006 Creation Date: 04-aug-2004 Expiration Date: 04-aug-2007
Domain Name.......... streamjobs.net
Creation Date........ 2004-08-05 Registration Date.... 2004-08-05 Expiry Date.......... 2007-08-05 Organisation Name.... Thierry Laurent Organisation Address. 422 Red River Trail Organisation Address. Apt 1075 Organisation Address. Irving Organisation Address. 75063 Organisation Address. TX Organisation Address. UNITED STATES
Admin Name........... Thierry Laurent Admin Address........ 422 Red River Trail Admin Address........ Apt 1075 Admin Address........ Irving Admin Address........ 75063 Admin Address........ TX Admin Address........ UNITED STATES Admin Email.......... tlaurent_us@hotmail.com Admin Phone.......... +1 (214) 7271499 Admin Fax............
Tech Name............ Thierry Laurent Tech Address......... 422 Red River Trail Tech Address......... Apt 1075 Tech Address......... Irving Tech Address......... 75063 Tech Address......... TX Tech Address......... UNITED STATES Tech Email........... tlaurent_us@hotmail.com Tech Phone........... +1 (214) 7271499 Tech Fax............. Name Server.......... ns1.globalservers.com Name Server.......... ns2.globalservers.com
It is not clear whether streamjobs.net is complicit in this scam, or whether their server has been hacked. The fact that they are hosting in Australia despite the domain being US-owned is suspicious: foreign hosting is one way of avoiding or delaying legal consequences for hosting illegal content.