Difference between revisions of "User:Woozle/2016/02/15/Postfix bounce-spam"
Jump to navigation
Jump to search
(note about SPF) |
(resolved?) |
||
| (One intermediate revision by the same user not shown) | |||
| Line 6: | Line 6: | ||
# [[/2016/02/14/21:32:58]] | # [[/2016/02/14/21:32:58]] | ||
# [[/2016/02/14/21:33:07]] (received right after #2; part of a sequence of 4 addressed to coinstar6116) | # [[/2016/02/14/21:33:07]] (received right after #2; part of a sequence of 4 addressed to coinstar6116) | ||
| + | |||
| + | Possible evidence: | ||
| + | * [[/tcpdump 1]] | ||
Some points of note: | Some points of note: | ||
| Line 13: | Line 16: | ||
* Both of those .org domains are configured with an {{l/wp|Sender Policy Framework|SPF}} host record to prevent messages with those domains being sent from anywhere except cloud2. | * Both of those .org domains are configured with an {{l/wp|Sender Policy Framework|SPF}} host record to prevent messages with those domains being sent from anywhere except cloud2. | ||
* Yes, we could probably eliminate most or all of the spam by disabling catch-all (i.e. only accepting email to certain addresses) -- but if the server is being abused to send spam, turning off catch-all wouldn't necessarily prevent that, ''and'' the abuse would become invisible to us. | * Yes, we could probably eliminate most or all of the spam by disabling catch-all (i.e. only accepting email to certain addresses) -- but if the server is being abused to send spam, turning off catch-all wouldn't necessarily prevent that, ''and'' the abuse would become invisible to us. | ||
| + | ==Update - Resolved?== | ||
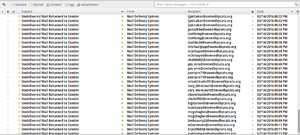
| + | More of the "ownedbycats" spam started arriving early this morning (2/16) and was still coming in by the time I got up, so I took another look at mail.log and found [[/mail.log 1]] -- which looks pretty clearly like someone logging in as user "harena", and using that to authorize sending messages. I changed harena's password, and the bounces stopped right away. | ||
Latest revision as of 14:16, 16 February 2016
Explanation / discussion: Google+
Sample emails:
- /2016/02/14/19:59:08
- /2016/02/14/21:32:58
- /2016/02/14/21:33:07 (received right after #2; part of a sequence of 4 addressed to coinstar6116)
Possible evidence:
Some points of note:
- Our mail server is cloud2.hypertwins.net.
- ownedbycats.org is one of the domains hosted on that server. (A complete list, from memory: hypertwins.com/net/org, ownedbycats.com/net/org, vbz.net)
- ownedbycats.org and hypertwins.org are both set for catch-all (i.e. will accept email to [any address]@[domain]).
- Both of those .org domains are configured with an SPF host record to prevent messages with those domains being sent from anywhere except cloud2.
- Yes, we could probably eliminate most or all of the spam by disabling catch-all (i.e. only accepting email to certain addresses) -- but if the server is being abused to send spam, turning off catch-all wouldn't necessarily prevent that, and the abuse would become invisible to us.
Update - Resolved?
More of the "ownedbycats" spam started arriving early this morning (2/16) and was still coming in by the time I got up, so I took another look at mail.log and found /mail.log 1 -- which looks pretty clearly like someone logging in as user "harena", and using that to authorize sending messages. I changed harena's password, and the bounces stopped right away.